Hardware Security Measures in Consumer Technology
In an increasingly interconnected world, the security of our personal data and digital interactions hinges not only on robust software but also on the underlying hardware. Consumer technology, from smartphones to smart home devices, integrates various physical safeguards designed to protect against unauthorized access and manipulation. Understanding these foundational hardware security measures is crucial for appreciating the comprehensive approach taken by manufacturers to ensure data integrity and user privacy in the digital age.
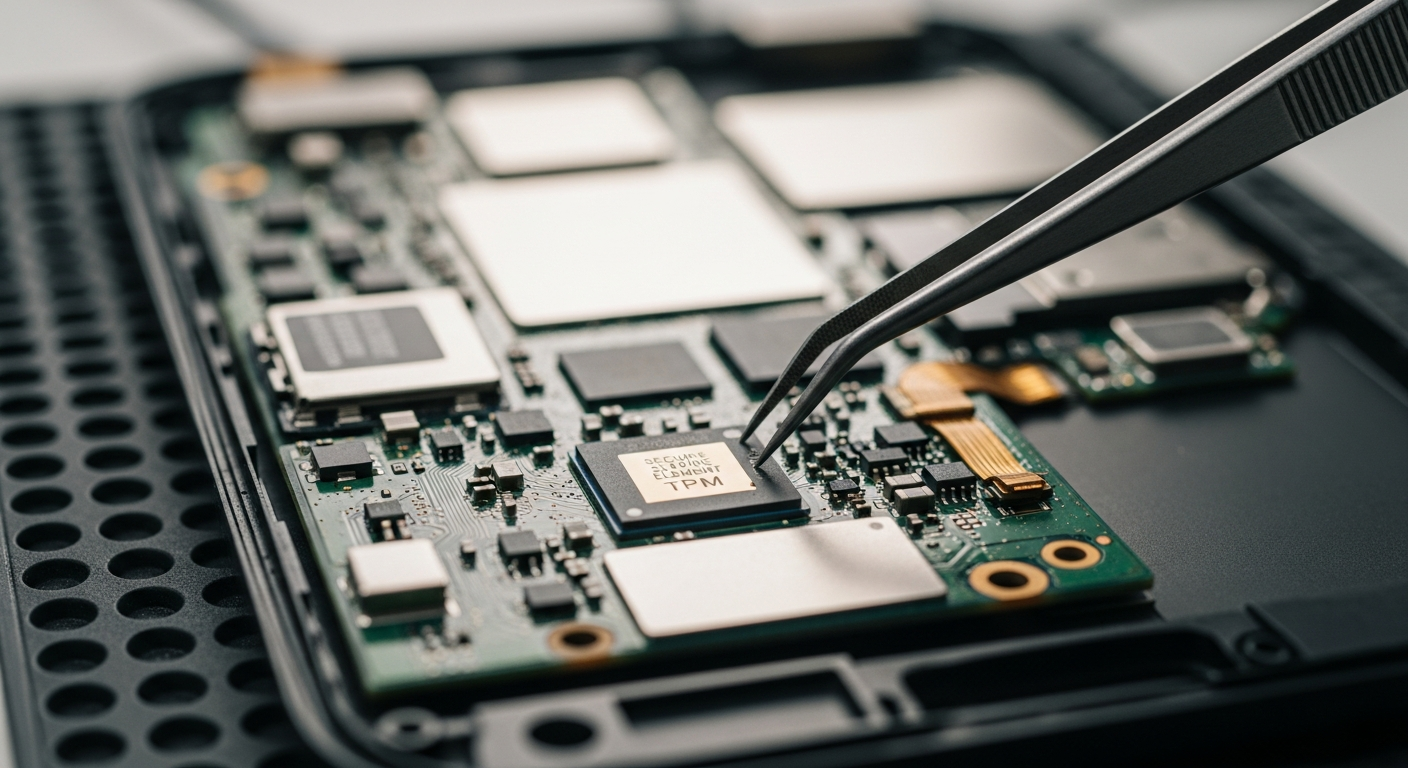
The widespread adoption of digital devices has amplified the importance of security beyond just software applications. Hardware security measures are critical components embedded within consumer technology, forming the first line of defense against cyber threats. These physical safeguards are designed to create a trusted execution environment, protect sensitive data, and ensure the integrity of the device’s operations from the moment it powers on.
Foundational Elements of Hardware Security
Modern consumer devices rely on several core hardware components to establish a secure foundation. Trusted Platform Modules (TPMs) are microcontrollers that store cryptographic keys, passwords, and digital certificates, enabling secure boot processes and disk encryption. Secure boot, a feature often integrated with TPMs, ensures that only legitimate, signed firmware and software can load during startup, preventing malicious code from taking control early in the boot sequence. Some advanced systems also incorporate Physically Unclonable Functions (PUFs), which leverage inherent manufacturing variations to create unique, device-specific identifiers for enhanced authentication and key generation, further bolstering the security of individual gadgets.
Protecting Data and Connectivity in Consumer Devices
Data protection is paramount in any digital ecosystem. Hardware-level encryption engines are often integrated directly into storage controllers, ensuring that data stored on solid-state drives (SSDs) or embedded flash memory is encrypted at rest without impacting performance. This means even if a device is physically compromised, accessing the raw data remains challenging. Furthermore, secure elements (SEs) are specialized, tamper-resistant microchips designed to securely store sensitive information like payment card details or biometric data for authentication. These elements isolate critical data from the main operating system, providing a highly protected environment for transactions and identity verification. Secure network interfaces, embedded within Wi-Fi and Bluetooth modules, are also designed to handle encrypted communications, safeguarding connectivity from eavesdropping and unauthorized access.
Innovations in Processor and System-Level Security
At the heart of every computing device are its processors, which increasingly incorporate dedicated security features. Modern CPUs, such as those with ARM TrustZone or Intel SGX (Software Guard Extensions), create isolated execution environments known as secure enclaves or trusted execution environments (TEEs). These enclaves allow sensitive operations, like cryptographic computations or handling of personal data, to occur in an environment isolated from the main operating system and other applications, even if the primary OS is compromised. This architectural innovation significantly enhances the protection of critical data and processes, making systems more resilient against sophisticated attacks. Memory protection units also play a role, preventing unauthorized access to memory regions by different processes, a fundamental aspect of system integrity.
Designing for Future Digital Security
Future advancements in hardware security are continuously evolving to meet emerging threats and the demands of miniaturization. The design process now heavily emphasizes supply chain security, ensuring that components are authentic and untampered with from manufacturing to deployment. Firmware integrity checks are becoming more sophisticated, allowing for over-the-air (OTA) updates to patch vulnerabilities securely. As devices become smaller and more integrated, the challenge lies in embedding robust security features without increasing complexity or cost. Innovations in secure packaging and hardware root-of-trust mechanisms are also crucial for maintaining integrity across the diverse landscape of connected systems and devices, pushing the boundaries of what’s possible in secure digital innovation.
User Interface and Access Control Mechanisms
The user interface is often the first point of interaction with a device, and hardware security extends to how users access their systems and data. Biometric sensors, such as fingerprint readers and facial recognition modules, are prime examples of hardware-based access control. These sensors capture unique biological data, which is then securely processed and stored, often within a secure element, to authenticate the user. The hardware directly handles the capture and initial processing of this sensitive information, ensuring it remains protected from software-level vulnerabilities. Additionally, secure input mechanisms, including specialized keyboards or touchscreens, are designed to prevent keylogging or screen-scraping, further safeguarding user credentials and interactions with the digital interface. Multi-factor authentication, when supported by hardware tokens or integrated biometric systems, adds another layer of defense, making unauthorized access significantly more difficult.
Hardware security measures are indispensable in the modern technological landscape, providing a robust defense layer for consumer electronics. From secure boot processes and encrypted storage to advanced processor features and biometric authentication, these integrated safeguards work in concert to protect sensitive information and maintain the integrity of our digital lives. Continuous innovation in this field is essential to counter evolving threats and ensure that the devices we rely on remain trustworthy and secure.






